The warehouse mobile app is a way for end users to have external devices (such as RF guns) to interact with D365FO to improve efficiency with warehouse tasks. I recently had the opportunity to do a deep dive into how this functionality was secured and wanted to give an overview and then a set of best practices for securing it.
Warehouse Mobile App Overview
Here is an overview of the setup and configuration:
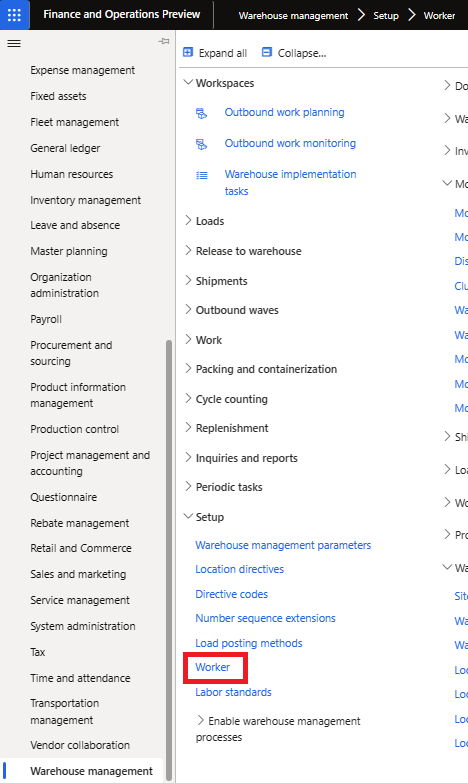
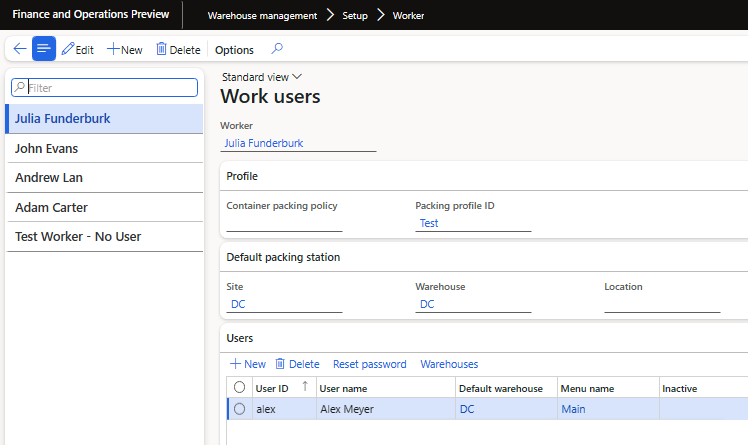
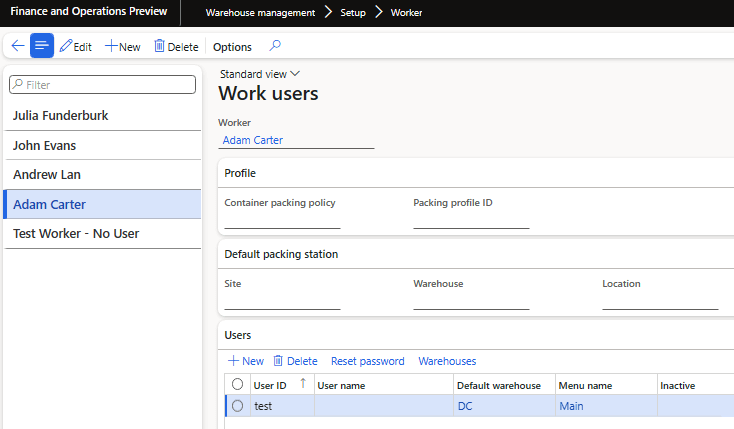
First we need to create a warehouse user by navigating to Warehouse Management -> Setup -> Worker:
Here you can create a warehouse worker based on a normal worker record and then create actual warehouse users. These warehouse users will have a separate UserID and password from their normal user accounts, this is also where you can assigned a default warehouse and the menu item assigned to the user.
The ‘menu item’ in this case is slightly misnamed as this is not a menu item in the sense of menu item displays, outputs, and actions. Instead it is a warehouse menu item within the mobile app itself.
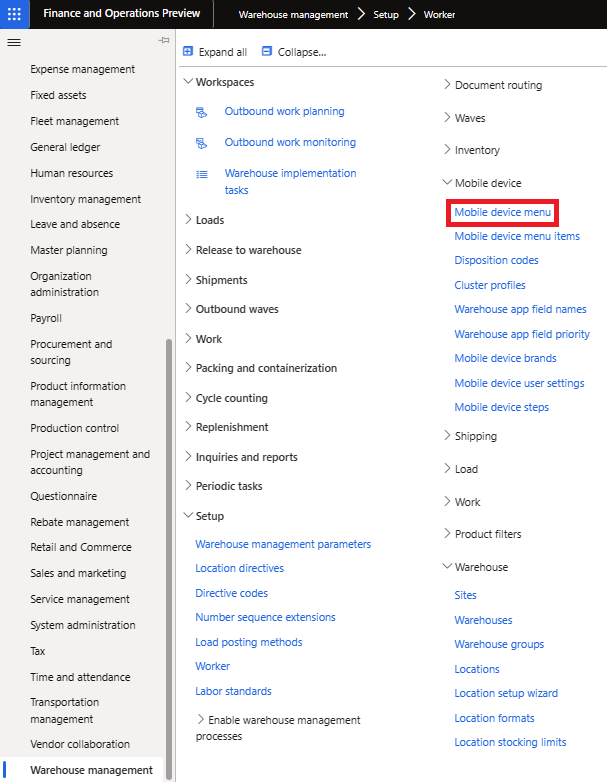
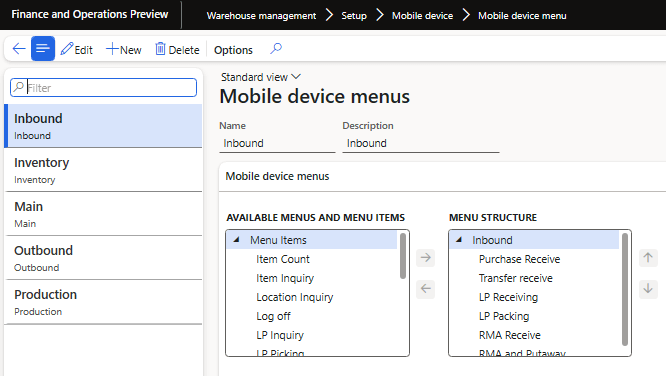
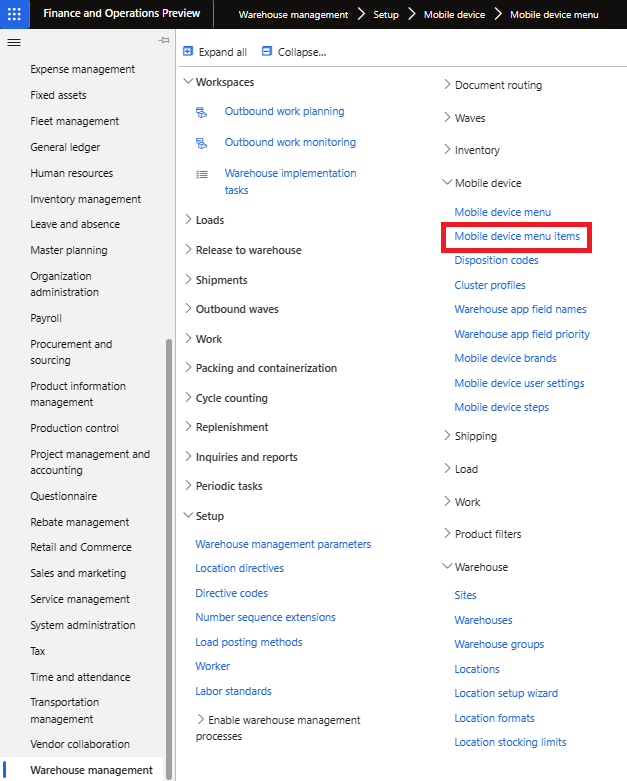
The menu structure can be found at Warehouse Management -> Setup -> Mobile Device -> Mobile Device Menu:
Here is where you can create the menu structure of the warehouse mobile app:
Note: You can have menus assigned to other menus to create a tree structure
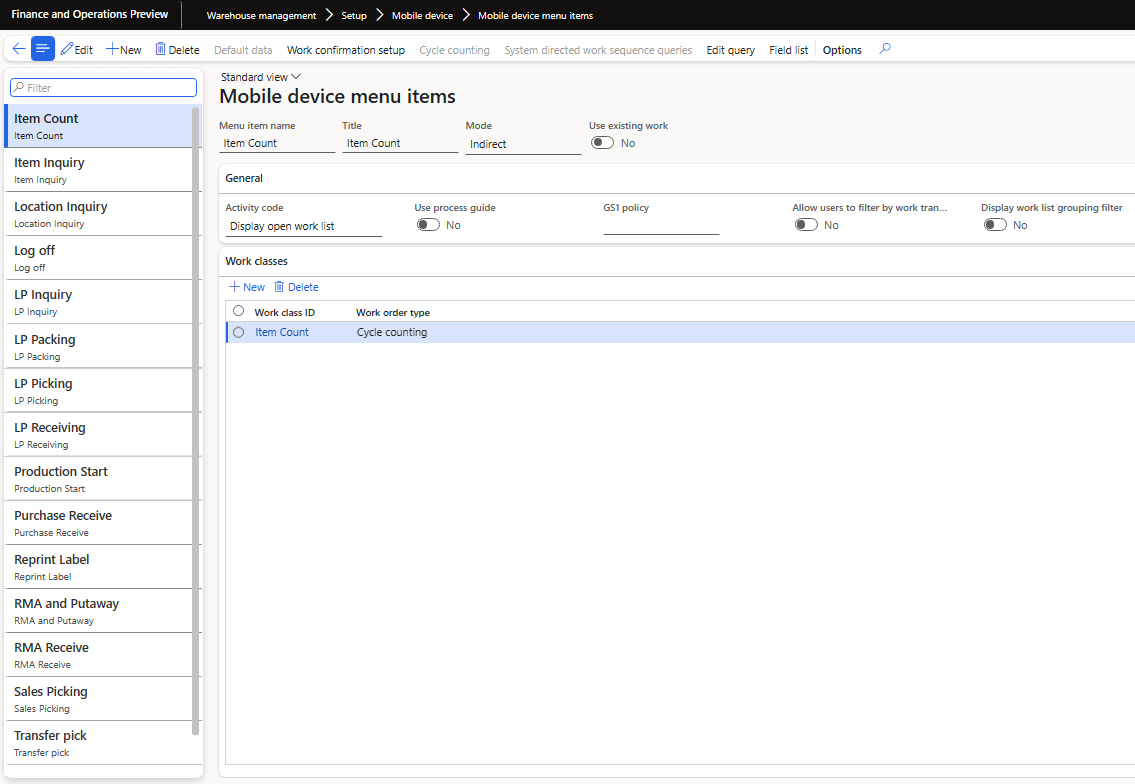
These menus just provide navigation within the mobile app, the actual menu items which perform the different warehouse functions can be found at Warehouse Management -> Setup -> Mobile Device -> Mobile Device Menu Items:
Here is where you can create ‘menu item’ entries in the warehouse mobile app. D365FO natively has some of these already created but clients have the ability to create additional entries:
Securing the Warehouse Mobile App
So now that we have a high level overview of the setup how do we secure it? Initially the thought was that since a worker record is required for the warehouse user setup that it would tie back to normal menu item based security. Through the testing below we found that to not be the case, the reason for this is because all of the different processes within the mobile app execute code and do load any forms through a menu item (which would cause security checks to be performed).
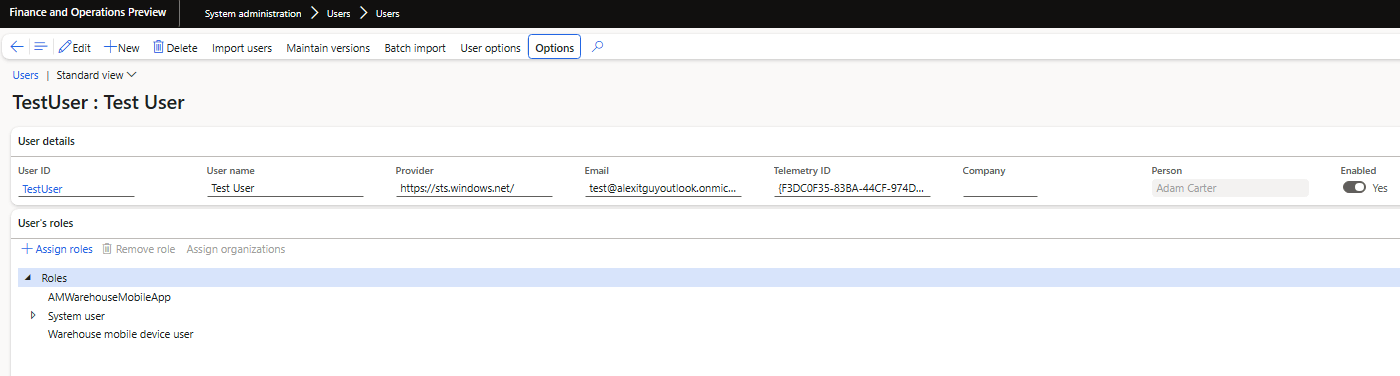
To test this, I first created a test user and assigned it the following roles:
- System User
- Warehouse Mobile Device User
- Custom Role to create access to the warehouse emulator (will explain more on this later)
I then associated this user with the ‘Adam Carter’ worker.
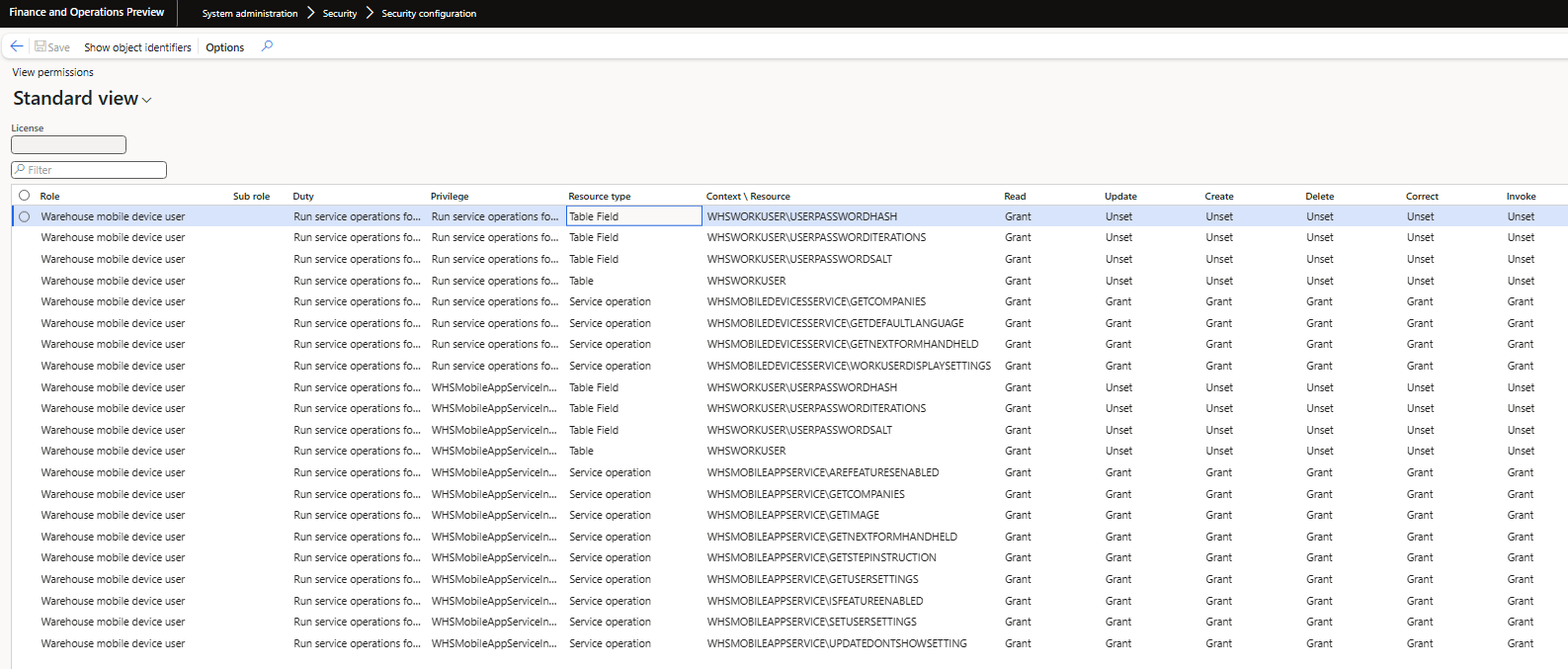
The Warehouse mobile device user role only contains access required to perform actions within the mobile warehouse application.
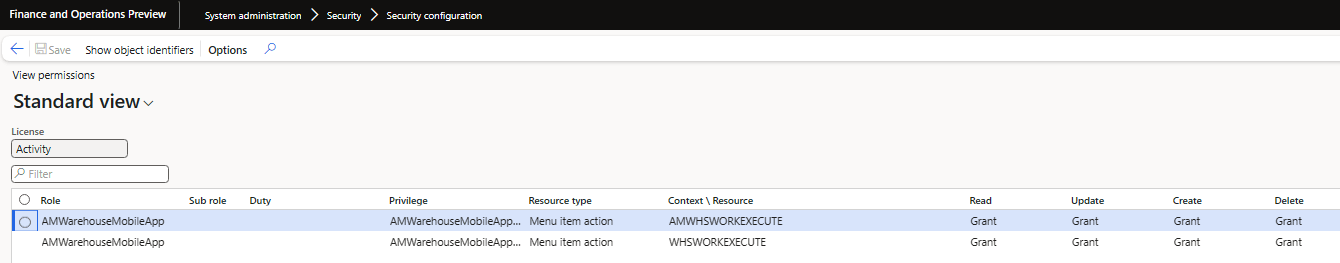
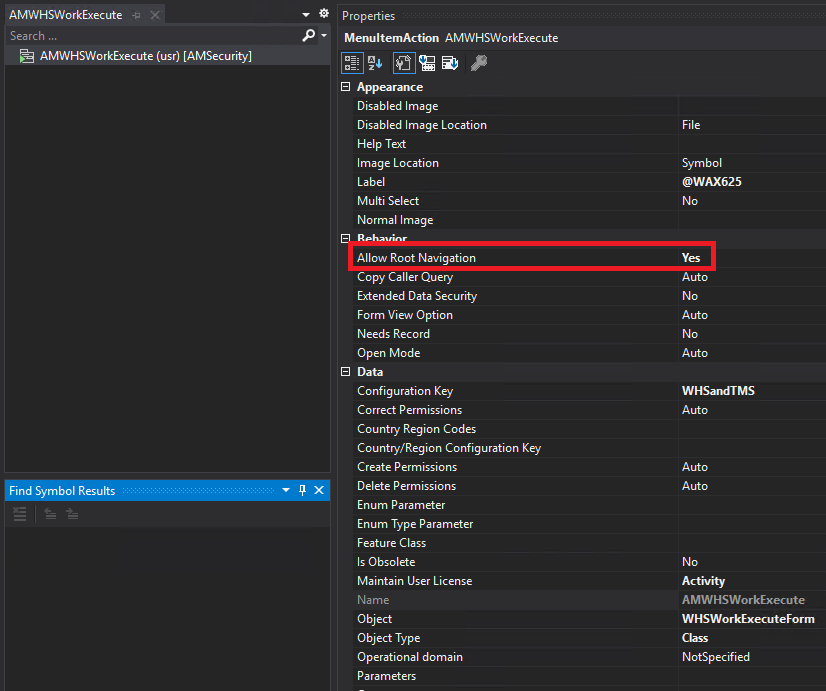
My custom role just has access to the WHSWorkExecute menu item (I ended up having to clone the menu item for a non-SysAdmin user to be able to navigate directly to it which is where the AMWhsWorkExecute menu item comes from but it is a clone of the base object and calls the same class).
The WHSWorkExecute menu item action does not allow for non-SysAdmin users to navigate directly to this menu item (the ‘Allow Root Navigation’ property is set to No) so to be able to correctly test this I had to clone this menu item (AMWHSWorkExecute) and set this property to ‘Yes’:
I then logged in as this test user.
And made sure to associate the Adam Carter user to a new warehouse worker (test).
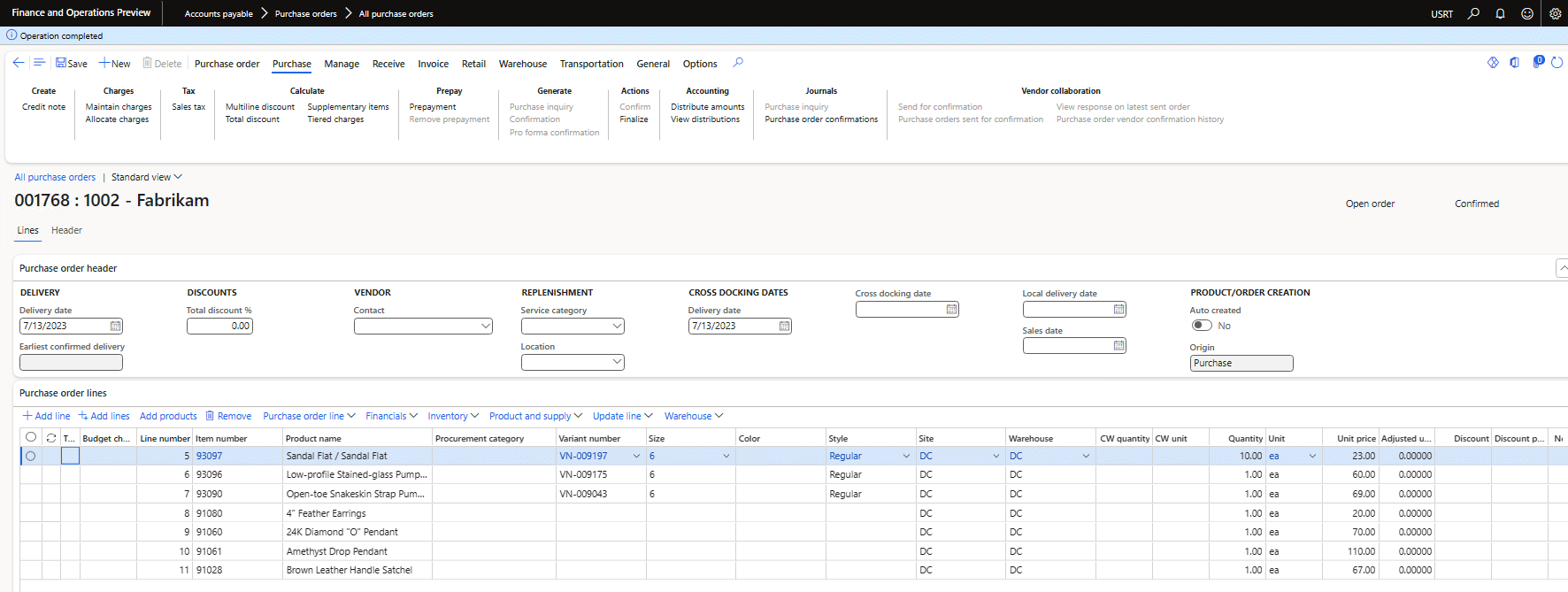
I then found a purchase order, that I could receive POs on:
Then I launched the warehouse mobile app emulator (by adding mi=action:AMWHSWorkExecute to the URL) and logged in to the ‘test’ user account:
Note that logins are company specific!!! I created this user in the USRT legal entity so this login will only work within launching the warehouse mobile app in the USRT legal entity.
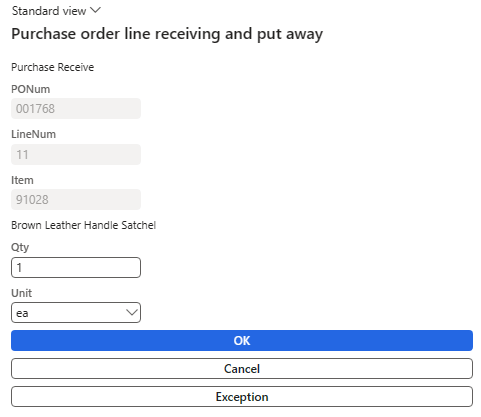
I then performed a PO line receiving and put away process:
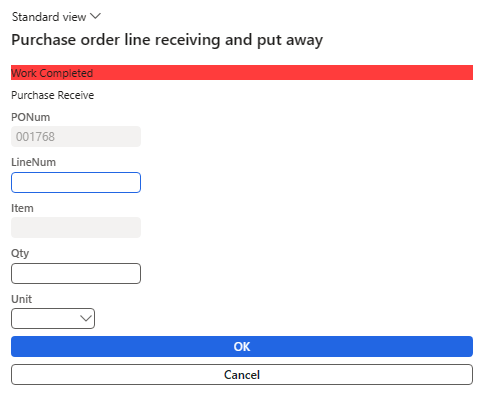
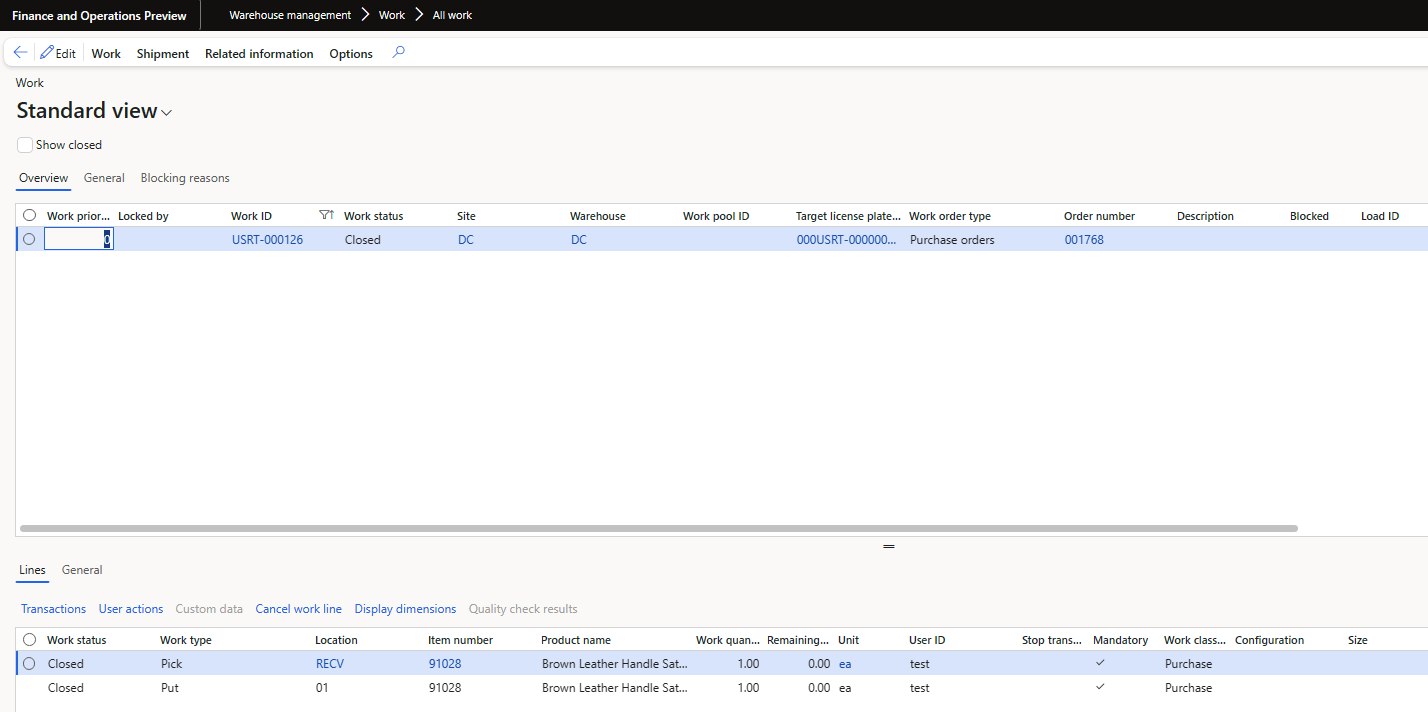
And you can see the work was completed successfully:
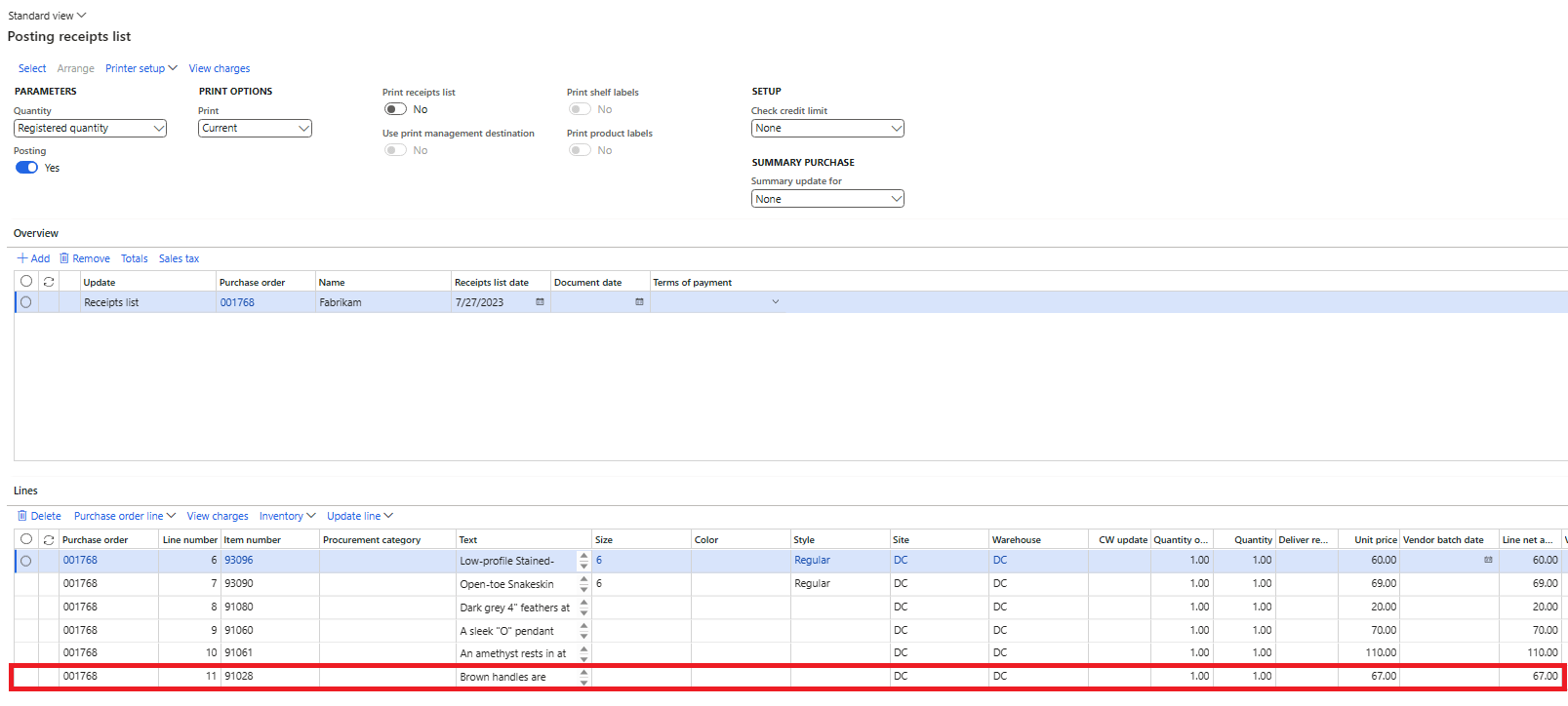
To verify the work was actually performed, I navigated to the Work Details form and was able to verify that the work was completed for PO 001768 for Item number 91028 (PO line 11 from above):
Second verification from the Posting Receipts list form:
Best Practices for Secure Warehouse Mobile App
Since the warehouse mobile app does not follow normal menu item security, how do we secure it? There has to be a combination of processes done to effectively secure it, which could include:
- Ensuring that separate worker IDs are being used for logging into the warehouse mobile app (no shared logins)
- Correctly identifying which mobile app functions a user should have access to and assign only that menu path to them
- Utilize out of box workflow functionality to help reduce risk when possible
- Review warehouse audit trail on periodic basis
What does your organization do to help secure the warehouse mobile app?