In AX 2012 you had the ability to use Active Directory groups to help manage security within the application.
The basic setup behind this was that you would:
- Create an AD group and put in the AX users you wanted to be controlled by that group
- Create the AD group within AX, that group would basically act as a user within the application
- Then create the users of that group as users within the application but assign them no security other than the System User role
- Configure the security for your AD group within AX, now anyone assigned to that group would automatically get assigned the roles assigned to that group
Here is a great overview of the setup of this functionality.
But what if you wanted to do the same process within D365FO with Azure AD groups?
Well we immediately run into an issue because out of the box this functionality is disabled, so how do we go about turning it on and getting it set up again?
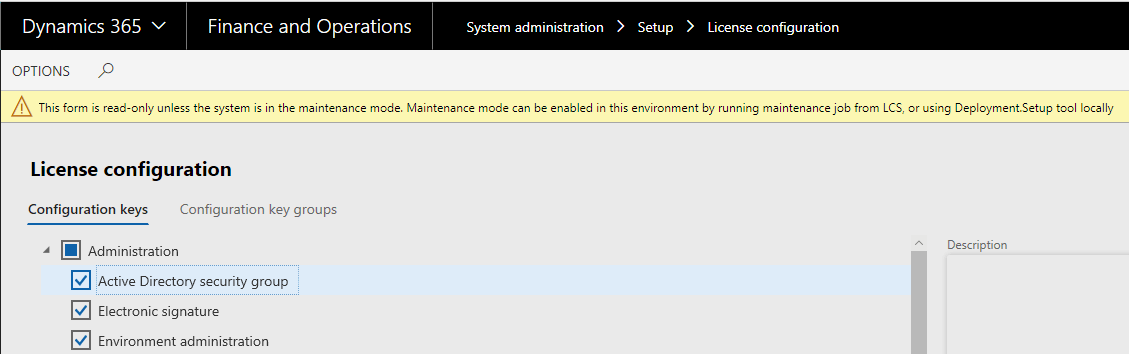
Step one is we have to put our environment into ‘maintenance mode’.
Putting Your Environment Into Maintenance Mode
The reason we have to do this is because we have to change a setting on the License Configuration page (found at System Administration -> Setup -> License Configuration) to enabled Active Directory Group Security and to do that we have to put our environment into maintenance mode. If you don’t do this, you will get this nice warning when you go to the page and you will not be able to actually edit any of the configuration values.
Currently the only way to do this is via command prompt, but it appears that in the future there will be a way to do this via LCS. Instructions for this process can be found here.
Once you enable maintenance mode and enable the Active Directory Security Group configuration value, make sure to disable maintenance mode and restart your AOS.
Group Security
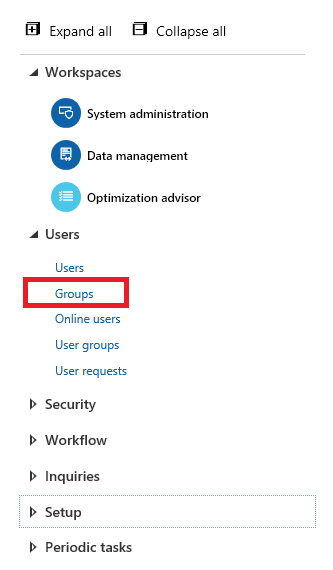
Now when you go to System Administration -> Users will have a new entry called Groups.
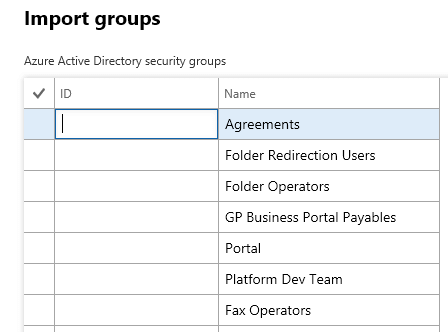
This page will look very similar to the Users setup screen, but you are setting up group security instead. The first thing to do is to import the Azure AD group you are looking to set up.
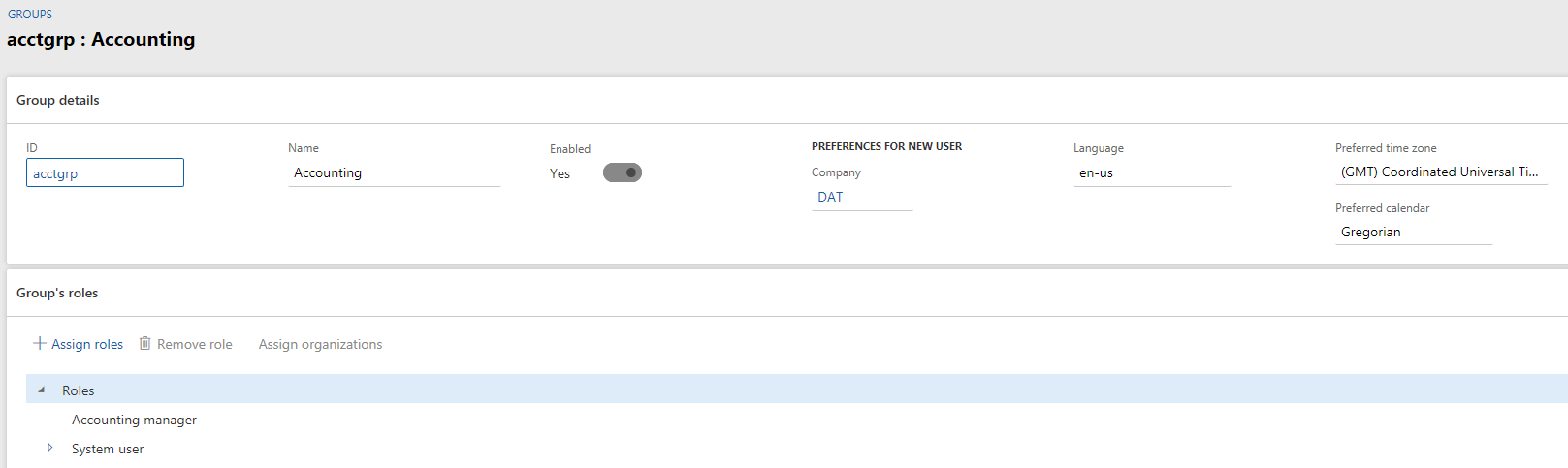
Once you select the group, you will notice the screen looks exactly like the User Info setup screen where you have a details area at the top and the roles you want to assign at the bottom.
Once this is setup the final step is to create each user of that group as a user within D365FO, but only assign them the System User role. Now going forward any user assigned to this group will automatically inherit the security the group has. In this way if you need to make a security change that will affect all users of a group you can make the change at the group level instead of going to each user one by one.
Things to remember
- Disabling an Azure AD Group does not disable users assigned to that group from logging in, only disabling the Azure AD user, removing the group as a user from within D365FO, or removing the D365FO user entirely will affect the user’s ability to sign into D365FO. There have been times where users think if they disable a group that all of the users assigned to that group will automatically lose access to AX/D365FO. This is not the case, the logic to determine group access only looks to see if the users are a part of that group not if the group itself is enabled. An entire forum post about this topic can be found here.
- All assigned access is cumulative, so if a user is assigned roles directly and is set up in an Azure AD group that is also assigned roles that user’s access will be a summation of both the directly assigned roles and the inherited roles from the Azure AD group.
- While this process can help with setting up user security, it can also make it more difficult to report on what access a user actually has. Because you have to make two separate reports, D365FO User -> Azure AD group assignment and Azure AD group access within D365FO (and remember the group is setup as if it were a D365FO user). Which if you’ve read previous posts of mine you know how difficult it is to determine user access within D365FO with the out of box reports available.
Note: A report like this one in Fastpath would help with this process, also all of Fastpath’s reports (including User and Role Access) fully support both AD group security as well as Azure AD group security setups in AX and D365FO.
I hope this post helped explain what the Azure AD group security functionality is, the benefits it can provide, things to look out for. If you have any questions about this please feel free to reach out.


Nice post Alex. We had already implemented this but we face an issue pertaining to WF. Since sec role is controlled thru grp the wf configured to those groups are failing. Any solution for this?
I believe workflows using security roles will not work when using Azure AD group security because users are not assigned roles directly as they get their security assignment through AD Groups. This page states that one of the prerequisites of using workflow is that you assign roles to users.
Hi,
Nice article and very useful, we had implemented in one of our project, but find issues in Workflows, when we assign Groups with security roles. Since Groups can not be associate to worker/person.Are we missing any configurations or setup for workflow?
I believe workflows using security roles will not work when using Azure AD group security because users are not assigned roles directly as they get their security assignment through AD Groups. This page states that one of the prerequisites of using workflow is that you assign roles to users.
Hi Alex
Thanks for the nice article, we did this setup and everything works. The only thing we are wondering is how does this affect the user license report that is used by MS to check user/role/license assigment? will this take into account that all users only have systemuser role and that other roles are linked using AAD groups?
David,
The licensing reports from Microsoft do not take into account AAD groups (as far as I know) so you would have to look at the D365FO license required for each AAD group and then do a mapping to each user in that group to determine the end user licenses.
If you are looking for a tool to help automate this type of reporting (along with a host of other security related things) you can check out the Fastpath Assure solution that I am a lead developer on.
Hi Alex,
Is it possible to use nested AAD Groups with D365? For example, our AAD groups are more granular then I would need in D365 security. For example, if I have 2 AAD groups for sales, AAD-Hunters (8 users) and AAD-Farmers (5 users), but in D365 they have the same security roles, can I create an AAD-Sales (13 users), and have the other 2 AAD groups role up? That way I can import just the AAD-Sales and set security on that one group.
Kellie,
I have not tested this but I guess I don’t see any reason why it wouldn’t work.
My biggest hesitation with this would be maintainability, because you run into the same thing when you start nesting roles on top of each other via subroles in D365FO natively. It becomes almost impossible to try and determine each user’s access (unless you have some automated tool like Fastpath) especially if you have any audit requirements as a business. Unless you have a very well defined process on being able to setup/maintain/and report on this setup I would shy away from getting too complex with AAD groups.
Hi Alex,
Great post, very informative! Does Fastpath (specifically D365FO) integrate with Azure AD so if a change is made to an Azure AD group that change would be represented in Fastpath (e.g., Identity Manager request)?
Amy,
Fastpath absolutely supports Azure AD groups in our security import process. For Identity Manager requests you would be able to change Azure AD groups a user is assigned via our IM integration for AAD not D365FO. This is an interesting scenario though that we could definitely walk though. Feel free to reach out via email and we can set up a call to go through it.
Hi Alex,
Thank you for this information. I just would like to ask, I have a role, but when it is assigned to the Group (AD group), some functionality doesn’t work, while when the role is assigned directly to the users, the functionality (that doesn’t work before) work on this kind of setup. Do you have any idea regarding why?
Hello,
Not sure what features what features you are having issues with but there are definitely some features that will not work when utilizing AAD group security security. Workflows and the segregation of duties are two examples of this as both require that the roles be assigned directly to the user for them to work. Can you elaborate on which features are not working in your scenario?